Hook, Line, and Sinker
The digital age, while teeming with advancements and opportunities, also opens the floodgates to new forms of security risks and cyber threats. Among the most prominent of these threats is phishing. Unfortunately, phishing is not about the thrill of the catch; rather, the catch becomes the thrill for cybercriminals. This blog post aims to equip you with the knowledge and skills necessary to effectively spot and avoid phishing scams, thereby enhancing your overall cyber vigilance. In the language of cybersecurity, “phishing” refers to a deceptive method that cybercriminals use to trick unwary people into disclosing sensitive information like usernames, passwords, credit card numbers, and other similar details. The attackers masquerade as trustworthy entities to reel in their victims through email, telephone, or text messages.
The Many Faces of Phishing
Not all phishing attempts are created equal. Some are broad, indiscriminate campaigns, akin to casting a wide net, while others are targeted and personalized, like fly fishing. The two most common forms are generic phishing and spear phishing. Generic phishing is widespread and typically involves impersonating a popular brand or service to trap an uninformed or less cautious user. Spear phishing, however, is much more dangerous and personalized, specifically targeting individuals or companies to trick them into divulging sensitive data. Also, spear phishing emails frequently contain personal information to make them sound legitimate. By understanding the different types of phishing, you can better identify and neutralize these threats.
Identifying Red Flags in Phishing Emails
Knowing how to identify phishing emailsis your first line of defense. Phishing emails often have some telltale signsthat can alert the vigilant reader. Let’s explore these red flags. Firstly,phishing emails often exhibit poor grammar and spelling, or unusual sentenceconstruction. This can be the first indication of a phishing attempt. Also, theemails usually sound too good to be true, like winning a lottery you neverentered, or urgently require you to take action, such as resetting a passwordor verifying an account to prevent it from being locked. If any email fills youwith a sense of urgency, then stop! Slowdown and look closely as it might be a scam.
Beyond the Obvious: Scrutinizing Phishing Emails
Beyond the obvious signs like poor grammar and urgency, phishing emails often contain mismatched URLs. Hovering over the link will reveal the actual URL, and if it doesn’t match the one written in the email, it’s likely a phishing attempt. Another red flag is a misspelled or slightly altered version of a well-known URL. For instance:
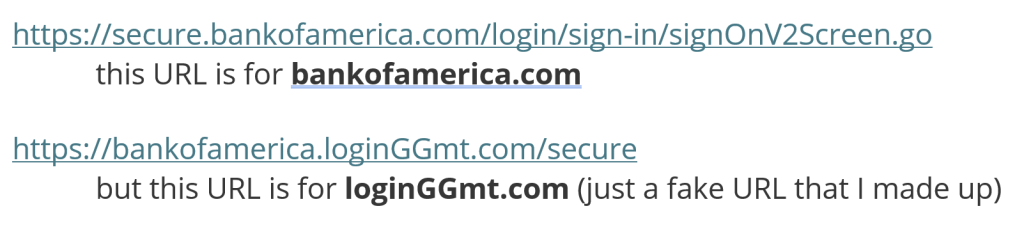
In the example above, note that the letters just before the .com (or .net, .biz, etc.) are the key. These letters are the actual website and not some subpage.
Moreover, the emails might use a generic greeting instead of addressing you by your name, indicating the sender does not actually know who you are. Also, be aware of any email that requests personal information, especially financial details. Legitimate organizations will rarely, if ever, ask for sensitive information via email.
Phone and Text Phishing: The Unsuspected Culprits
Phishing is not confined to emails. Cybercriminals often employ phone calls and text messages as their phishing mediums. This is known as vishing (voice phishing) and smishing (SMS phishing), respectively. Like email phishing, these attacks play on urgency, fear, and the human tendency to act before thinking when facing a supposed crisis. The attackers might pose as your bank, alerting you to suspicious transactions, or as a government department insisting on urgent action to avoid fines. Always approach unsolicited communication with skepticism. Instead of reacting impulsively, take the time to verify the information independently by reaching out to the relevant institution through their official contact methods.
The Social Media Trap
In this era of digital interconnectivity, social media has become another hunting ground for phishers. They create fake profiles, impersonate trustworthy entities or friends, send malicious links, or ask for sensitive information. It’s essential to be cautious when accepting friend requests from unknown people and to verify unexpected requests from existing contacts. Always scrutinize the information you share online, as phishers may gather it and use it for personalized attacks.
Bolstering Your Defense – Anti-Phishing Measures
Awareness is key in combating phishing, but combining it with proactive measures creates a solid defense. This involves keeping your system and security software updated, using strong, unique passwords for different accounts, and employing two-factor authentication wherever possible. Moreover, consider using a reputable email filter to weed out potential phishing emails.
For businesses, the below list of safeguards is the best-case scenario for phishing protection:
1. Strong email filter to reduce actual Phishing emails
– However, users not used to seeing phishing emails may be more easily tricked by an email that gets past the filter so…
2. Run a fake-phishing email campaign. While these emails look legit, folks that accidentally click links in the emails will not be hurt. They’ll only be educated. This keeps users vigilant for fake emails.
– However, don’t do this constantly as it can be a time waster. Education is good. Beating-over-the-head is bad.
3. Implement a company-wide password manager. Password managers will not submit credentials at a scam site masquerading as a legit website. This greatly helps reduce the chances that you or your team gives login credentials to a fake site. https://1password.com/ is one we like a lot.
4. Enforce MFA (Multi-Factor Authentication) on any login. If you do nothing else, do this.
5. Install a managed Endpoint Detection and Response solution (EDR, MDR, or XDR). If the worst happens and the computer is attacked, this is a very strong line of defense. Think of it like antivirus software… but that doesn’t require definitions. It’s superb.
Responding to Phishing Attacks
Despite your best efforts, you may still fall victim to a phishing scam. If that happens, don’t panic. Respond quickly by contacting your bank or the related institution to secure your accounts. Change your passwords immediately and monitor your accounts for suspicious activity. It’s also important to report phishing attempts to the respective institution’s fraud department and to local law enforcement agencies. This helps them take action against the culprits and protect others from falling prey.
Your Vigilance, Your Shield
Phishing attacks can be frightening and dangerous, but by practicing vigilance and awareness, you can significantly reduce the risk. Remember, in the digital world, knowledge is your armor, skepticism is your sword, and vigilance is your shield. Stay safe and stay alert!
